- Mike represents an organization which wishes to implement ISO 27001.
- Carol is an ISO 27001 consultant.
- Ann is an ISO 27001 lead auditor.
Mike has questions for each of the following points. Some are responded by Carol and the others responded by Ann.
Mike: Hi Carol and Ann, thanks for joining me today. Our organization is planning to implement ISO 27001, and I have quite a few questions to better understand the process.
Carol: Hi Mike! As an ISO 27001 consultant, I’m here to help you navigate the implementation process and ensure your organization is well-prepared for certification.
Ann: And as a lead auditor, I’ll address your questions about the certification process, audits, and how to maintain compliance once certified.
Mike:Let’s start with the basics. What is ISO 27001 certification?
Carol:ISO 27001 certification is a formal recognition that your organization has implemented an Information Security Management System (ISMS) that meets the ISO 27001 standard. It ensures you have a systematic approach to managing sensitive information securely.
Ann:It also means an accredited certification body has independently audited your ISMS and confirmed its compliance with ISO 27001.
Mike:Why should we implement ISO 27001?
Carol:It helps you manage information security risks, protects sensitive data, and enhances customer trust. It’s also essential for regulatory compliance, and gives you a competitive edge. Also consider all the opportunities you are perhaps you are loosing because you don’t have the ISO 27001.
Ann:From an auditor’s perspective, it demonstrates your organization’s commitment to security and continuous improvement. It’s especially valuable for industries handling sensitive information, like IT or finance.
Mike:Carol, what’s your role as an ISO 27001 consultant?
Carol:My job is to guide you through the ISO 27001 implementation process. I’ll conduct a gap analysis, help you design your ISMS, create necessary documentation, train your team, and prepare you for the audit. Think of me as your partner in achieving certification.
Mike:What is the difference between ISO 27001 and ISO 27002?
Ann:ISO 27001 defines the requirements for an ISMS, while ISO 27002 provides detailed guidance on how to implement the controls listed in ISO 27001’s Annex A. They complement each other.
Carol: Exactly. ISO 27001 is about the "what" you need to do, and ISO 27002 is about the "how"
to do it.
Mike:How does ISO 27001 differ from NIST or SOC 2?
Carol:Consider each standard as a Venn diagram. Each standard has something familiar with the other but has additional requirements for each. ISO 27001 is a good starting point for any organization, and you can implement other standards in a step-by-step manner.
Mike:What is an ISMS, and how do we create it?
Carol:An ISMS is a structured framework of policies, procedures, and controls to manage and mitigate information security risks. You create one by defining its scope, conducting risk assessments, implementing controls, and continuously monitoring and improving the system.
Ann:A well-documented ISMS is critical, as it will be the focus of your ISO 27001 audits.
Mike:What are the first steps to start implementation?
Carol:Begin with a gap analysis to assess your current security posture. Define the scope of your ISMS, create a risk assessment methodology, and establish a project plan.
Ann:Don’t forget to secure top management support early on. Their commitment is essential for success.
Mike:How should we define the scope?
Carol:Identify the processes, systems, and locations that handle information assets. The scope should align with your business objectives and risk exposure. The scope consists of the business/legal entity that is getting certified, business services, internal functions, locations and even networks.
Ann:A clear, concise scope makes audits more straightforward and avoids unnecessary complexities.
Mike:What’s the Statement of Applicability, and why is it important?
Ann:The SoA lists all Annex A controls, specifying which ones are applicable to your organization and why. It’s a critical audit document, as it demonstrates how you’ve tailored your ISMS to your specific needs. SOA also specified the controls that do not apply with their justification for exclusion.
Carol:It also serves as a reference for internal stakeholders, ensuring everyone understands the chosen controls and their purpose. Each control that is listed should undergo risk assessment, measurement and audit.
Mike:What are ISO 27001 management system requirements?
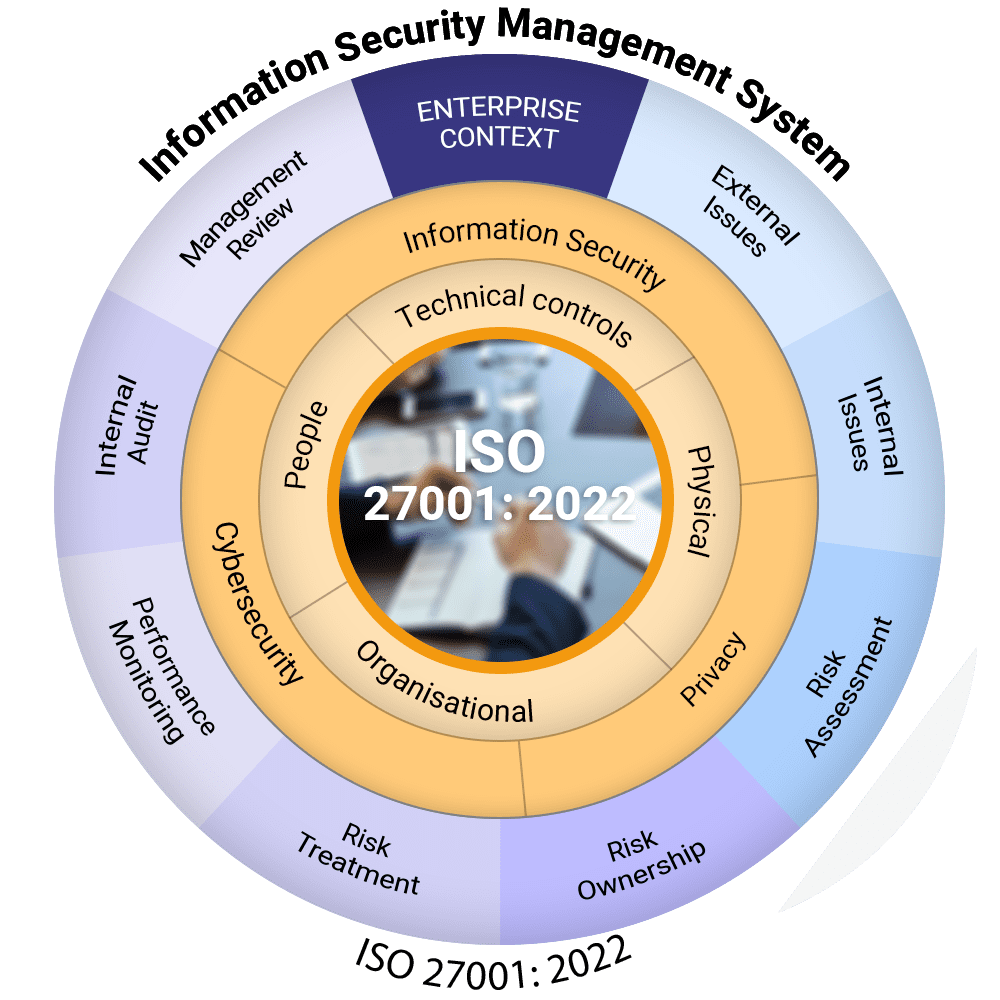
Carol:ISO 27001 Management System consists of context, interested parties, scope, ISMS policy, risk assessment, risk treatment, objective settings, measurements, internal audits and management review. To get ISO 27001 consider management system as mandatory requirements.
Mike:What are Annex A controls, and how do we determine which ones apply?
Carol:Annex A includes 93 controls across 4 domains of organizational security, human resource security physical security and technical controls. You select applicable controls based on your risk assessment.
Ann:The SoA will document which controls are relevant and why. This alignment between risks and controls is essential for certification.
Mike:How long does it take to get ISO 27001 certified?
Ann:It depends on your organization’s size and readiness. A startup can take 2- 3 months, whereas a multinational organization can take 9-12 months.
Carol:With proper planning and a committed team, you can streamline the process and achieve certification faster.
Mike:What happens once we’re certified?
Carol:Certification is just the beginning. You’ll need to maintain and improve your ISMS, conduct regular internal audits, and prepare for annual surveillance audits.
Ann:Compliance is an ongoing effort. Continuous improvement ensures your ISMS remains effective and adapts to evolving threats.
Mike:How do we demonstrate continual improvement?
Carol:Once you get certified, you will experience your ISMS journey. Based on this you will determine controls that require ongoing monitoring and others for occasional monitoring. For example you may decide to perform an access review every 3 months, 6 months or even once in 12 months. You will need to create a plan and execute and monitor the plan to ensure newly identified risks are treated urgently.
Mike:Thank you, Carol and Ann. This has been incredibly insightful. I feel much more confident about starting our ISO 27001 journey.
Carol:Glad we could help, Mike. Let’s get started on your implementation plan!
Ann:Looking forward to supporting you through the certification process. Let us know how we can assist further.