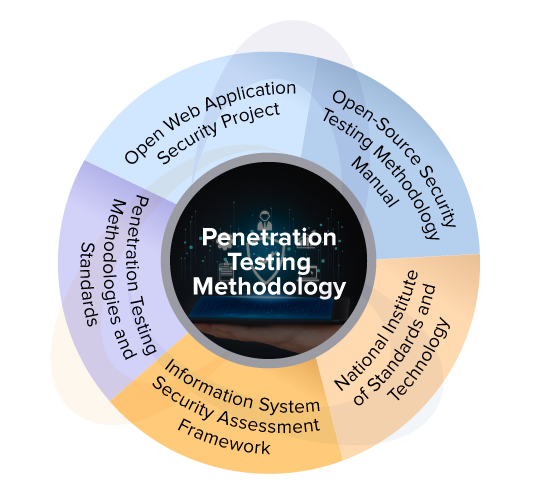
Penetration Testing Methodology
Our Penetration testing process was created in accordance with several internationally accepted frameworks/standards
- Open Web Application Security Project (OWASP),
- Open-Source Security Testing Methodology Manual (OSSTMM),
- National Institute of Standards and Technology (NIST),
- Information System Security Assessment Framework (ISSAF), and
- Penetration Testing Methodologies and Standards (PTES)
The role of these standards is to harmonize and provides users of the report with standardization. For instance, using OWASP references in the report, you can measure the risk associated to Top 10 OWASP attack vectors