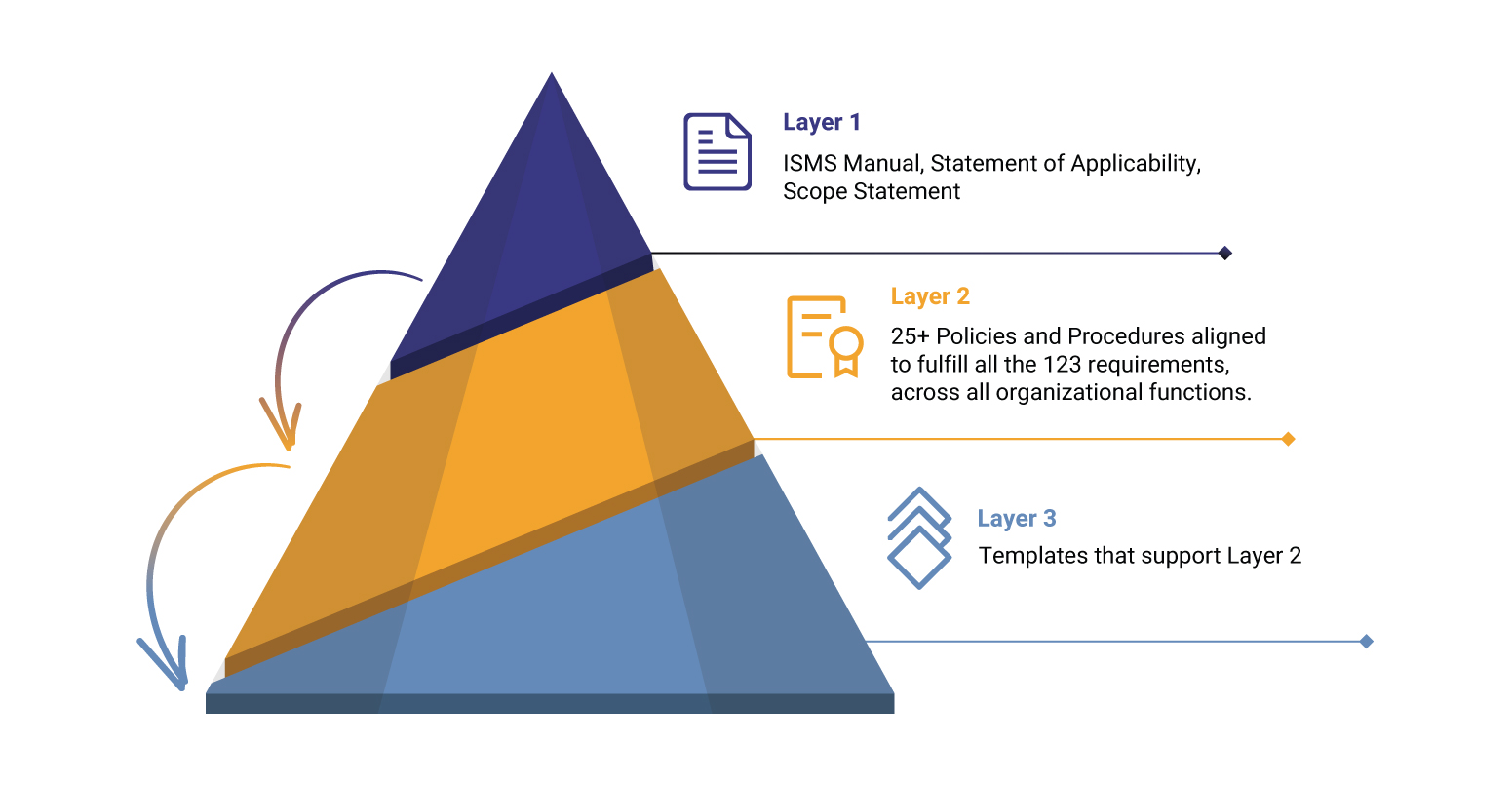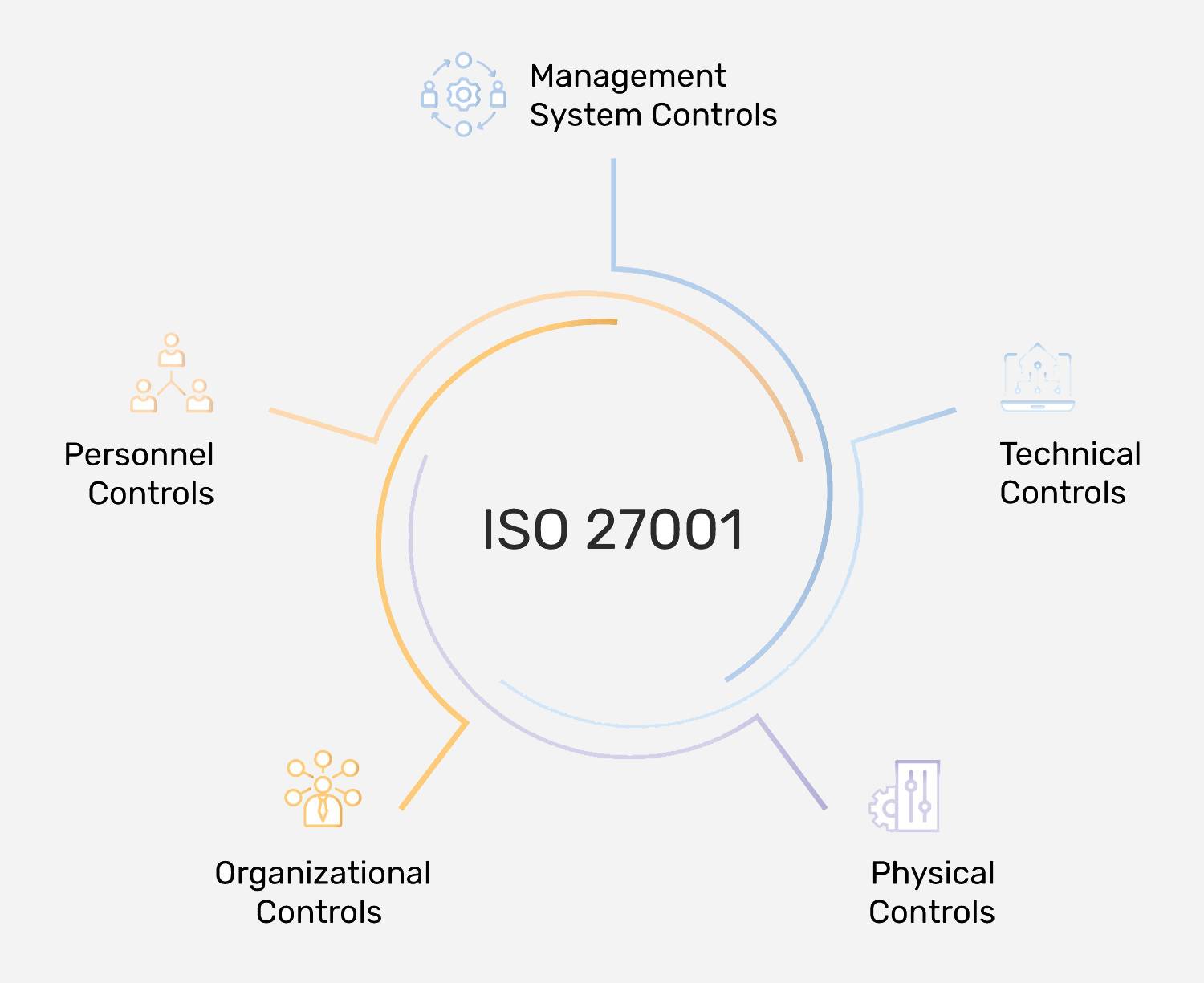
- ISO 27001 has 123 requirements. The toolkit has content to support all management system requirements (Clause 4 to 10), and Annexure Controls (5 to 8), covering 123 addressable requirements.
- The toolkit addresses all organizational functions
We have done the mapping of controls as per any organization structure. This consists of control distribution by teams such as Sales and Business Development, Top Management, Application development, IT Operations, Cloud, Human Resources, Physical Security, Supplier Management, CISO and even an Internal Audit. -
How do you map all the controls with organizational teams?
- As part of the toolkit, we provide a template for organization nominations. using this you can nominate members of the organization.
- Controls are mapped to organization nominations. This means if you nominate Alice as CISO, and Bob for HR controls, using the template Bob and Alice can see their applicable controls and applicable policies that they need to implement.